Subtotal $0.00
WhatsApp Privacy Settings — A Visual Guide
Introduction: this visual guide explains how each of the key WhatsApp privacy settings lowers the risk of WhatsApp hacking, walks you through each one, and demonstrates what to look for when using WhatsApp monitoring (both for enterprise security teams and for personal safety). I’ve provided a brief frequently asked question at the end, clear internal links (step-by-step instructions), and suggested image ideas for each screen so you or your designer can create visuals.

Why privacy settings are important (and how WhatsApp hacking is related to them)
Your primary line of defense against hackers who try to access your account through account takeover, social engineering, or zero-click methods is privacy settings. Proper settings make it more difficult to hack WhatsApp, decrease the attack surface (fewer exposures), and enable security teams to identify irregularities more quickly through WhatsApp monitoring.
Check out our in-depth article on how zero-click WhatsApp exploits operate at /how-zero-click-works if you want the complete technical background on zero-click threats.
If you suspect a compromise, check out our emergency recovery checklist: /whatsapp-emergency-checklist emergency checklist after WhatsApp compromise.
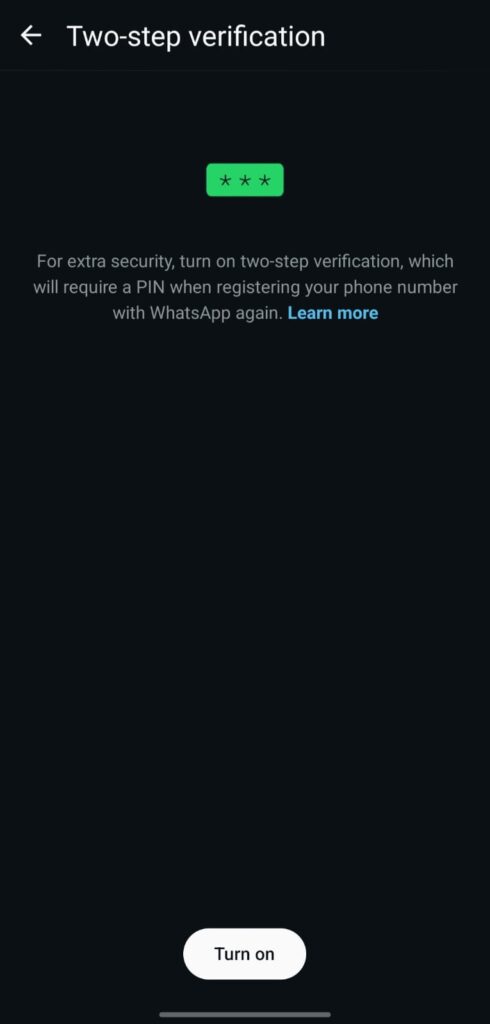
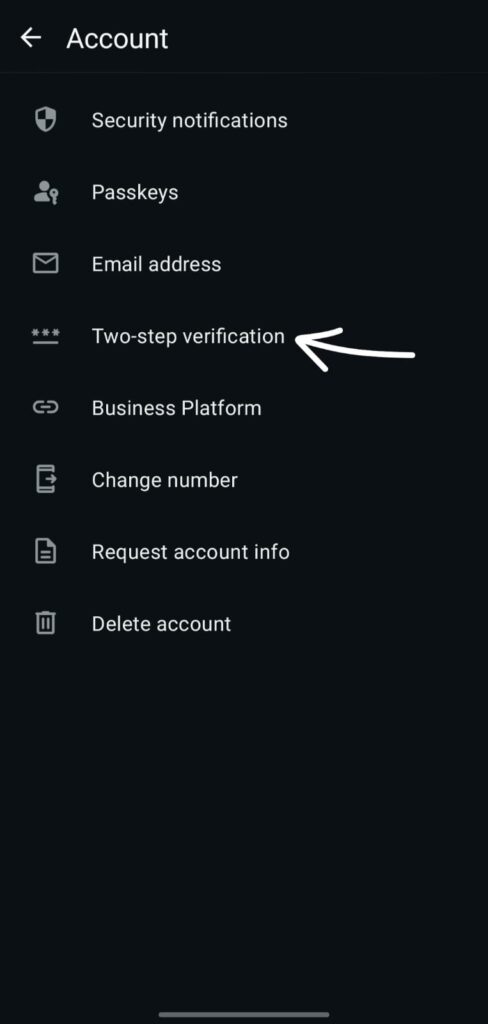
1) Account → Verification in Two Steps (MUST DO)
What: Makes it difficult for hackers to re-register your number by adding an additional PIN (and optional email).
Why it’s important stops account takeovers and SIM swapping, which are frequent components of WhatsApp hacking campaigns.
Setting it up: WhatsApp → Settings → Account → Two-step verification → Turn on → Select a recovery email and a strong PIN.
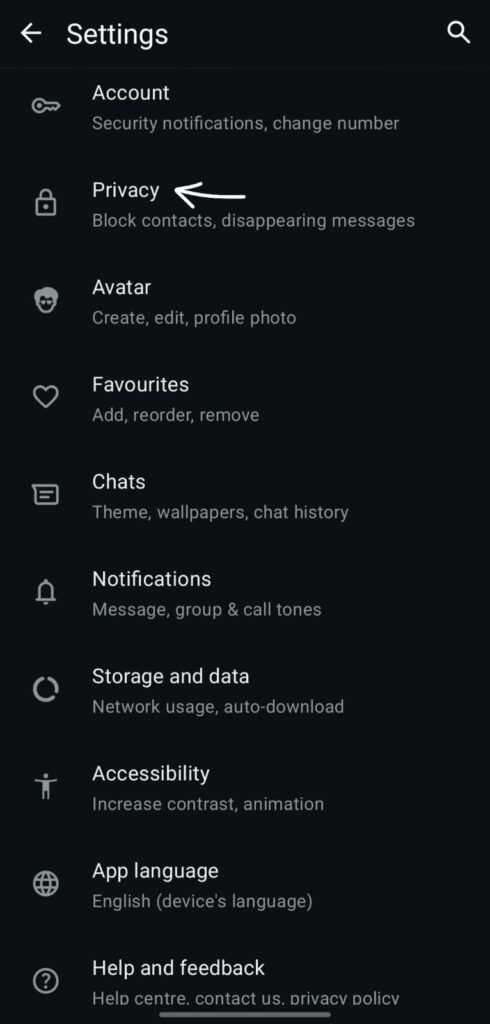
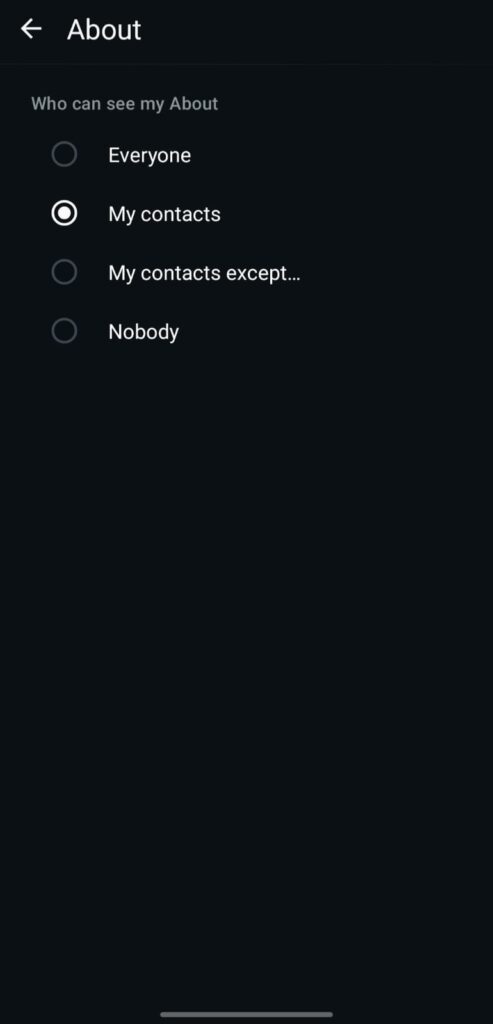
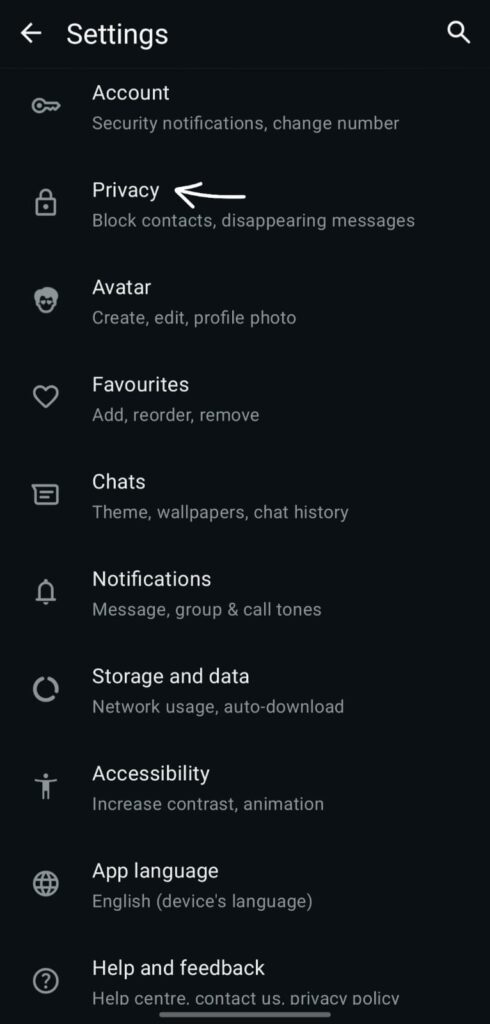
2) Account → Privacy: About (either "My Contacts" or "Nobody"), Last Seen, and Profile Photo
What: Regulates who can view your About text, Profile Photo, and Last Seen.
Why it’s important Public visibility helps attackers discover active targets and craft social attacks (or broaden reach for automated scanning). Reducing visibility lessens the likelihood of targeted approaches that result in WhatsApp hacking and makes you harder to track.
Setting it up: Settings → Account → Privacy → Last Seen / Profile Photo / About → Choose My contacts or Nobody.
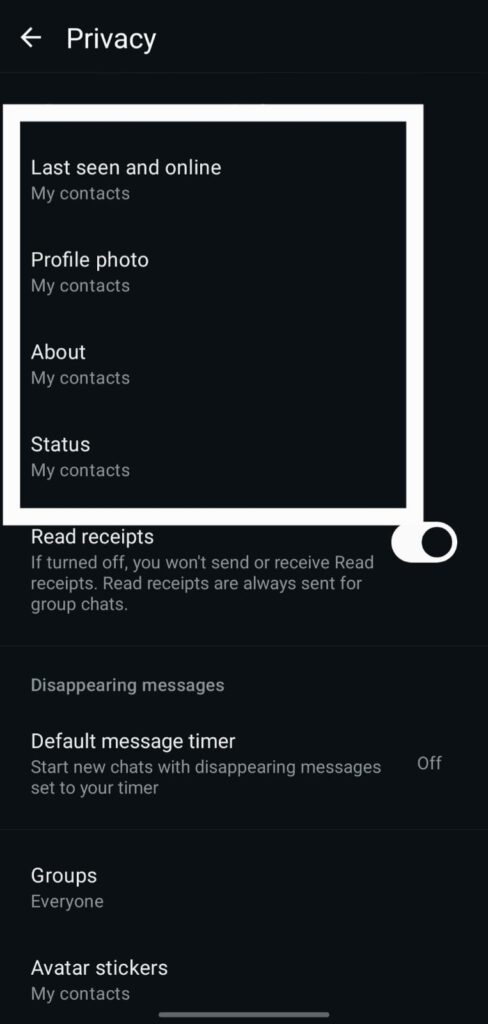
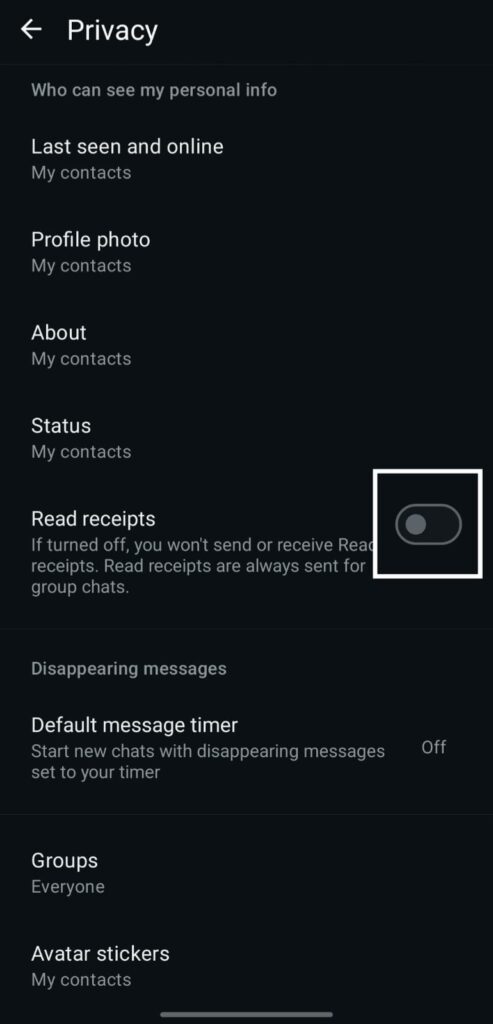
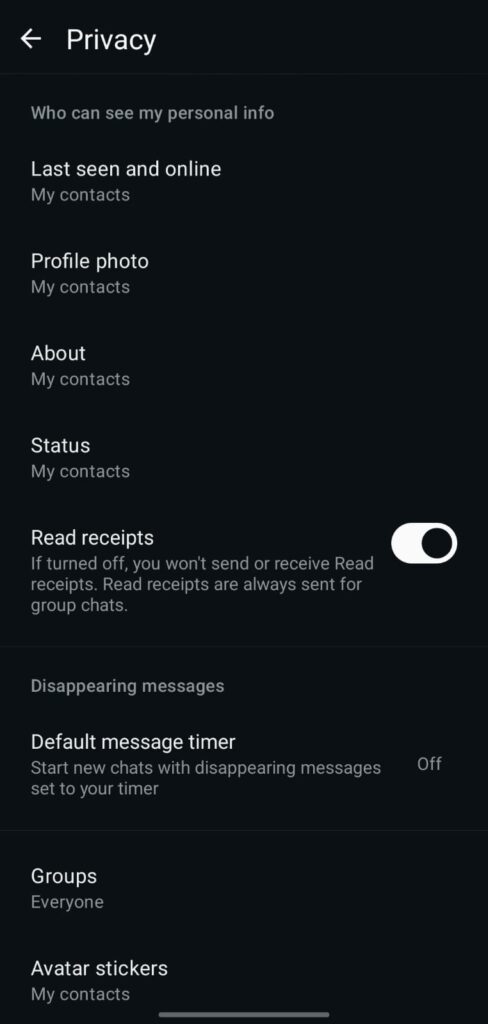
3) Examine the receipts (turn off for personal safety).
What: If you opened a chat, read receipts (blue ticks) indicate it.
Why it’s important If an adversary is watching you, turning them off will help them understand your activity patterns. (Note: Read status is always displayed in group chats.)
Setting it up: Settings → Account → Privacy → Read Receipts → Turn Off.
4) Profile Picture and Unknown Contact Visibility
What: Ensure that no one, or just contacts, can see your entire profile.
Why it’s important Attackers create convincing social engineering messages using profile information in order to facilitate WhatsApp hacking.
Setting it up: Settings → Account → Privacy → About → My Contacts or No One.
5) Groups: Who Can Invite You (Control Group Invitations)
What: Select if you want to be added to groups by Everyone, My Contacts, or My Contacts Except.
Why it’s important Mass spam or malicious group invites are two ways that attackers can spread exploit payloads or cause account churn. Reducing the number of unsolicited entries and exposure to unknown senders is achieved by limiting the number of invites.
Setting it up: To filter out unknown numbers, select My Contacts or My Contacts Except… under Settings → Account → Privacy → Groups.
6) Live Location: Only disclose when required
What: Contacts can track your location in real time with Live Location.
Why it’s important Constant sharing puts your privacy at risk and can be exploited by attackers or stalkers to identify your offline habits. Share only for brief, specified times.
Setting it up: Launch a conversation → attach → Location → Share the current location → Choose a duration (or cancel).
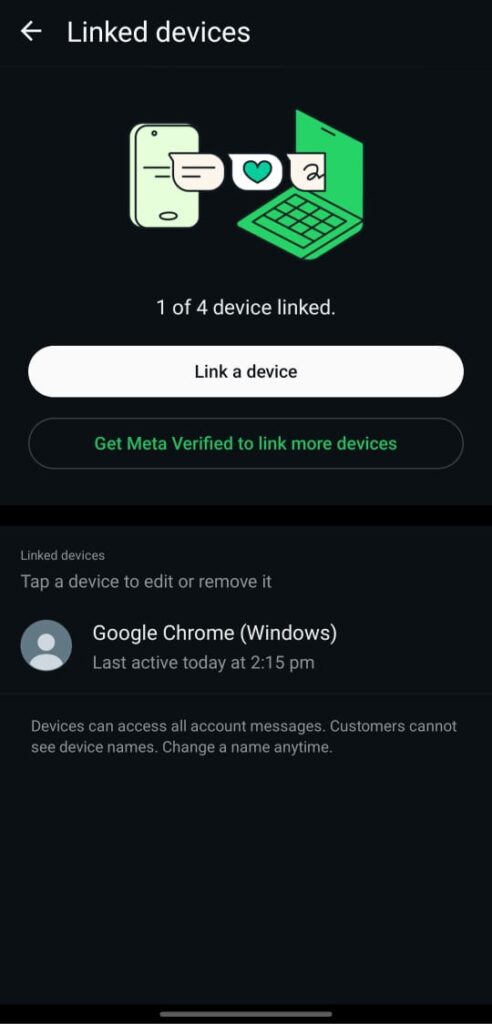
7) Connected Devices: Track and Terminate Unknown Sessions (Critical for WhatsApp tracking)
What: displays every device that has your active WhatsApp account (Desktop/Web).
Why it’s important Unknown linked devices are crucial for WhatsApp monitoring since they are a clear indication of compromise or abuse.
How to check or set: Settings → Linked Devices → Review List → Log out of any sessions that seem suspicious or unfamiliar right away.
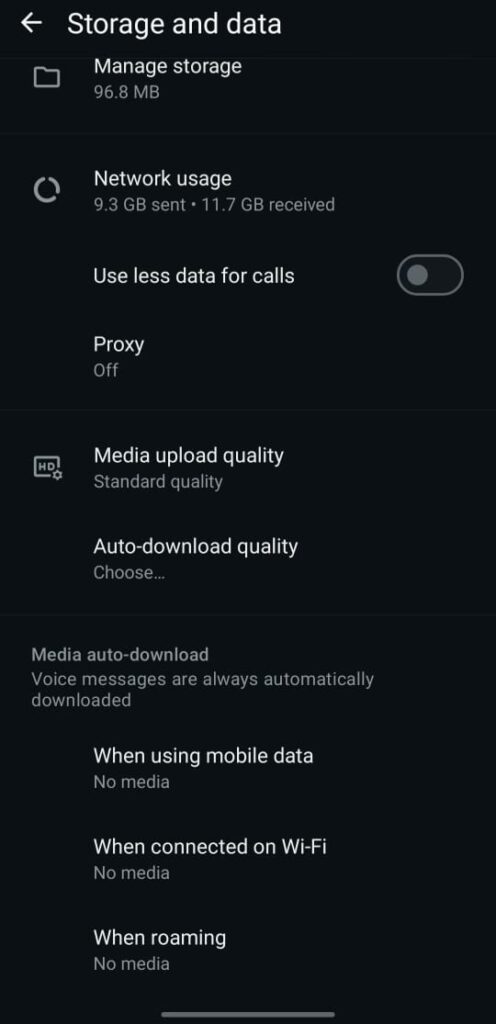
8) Media Visibility & Auto-Download (Decrease Automatic Parsing)
What: Manage whether videos, audio, and images download automatically over cellular or Wi-Fi networks.
Why it’s important Automatic media processing is necessary for certain zero-click or parsing-based vectors. Turning off auto-download lowers the possibility that malicious media will be silently parsed by your device.
Setting it up: Settings → Storage and Data → Media auto-download → Turn off for documents, audio, video, and photos (if desired).
9) View Once Media & Disappearing Messages (Reduce data retention)
What: View Once stops media from being saved locally after it has been opened once; disappearing messages delete content after a predetermined amount of time.
Why it’s important restricts the amount of time that private messages and attachments stay on your device in the event that it is compromised. useful for lowering the amount of data that spyware installed through WhatsApp hacking can access.
Setting it up: Launch chat → Tap contact name → Messages that vanish → Select duration. Send media → tap the view-once icon to enable view-once.
10) Block & Report — Immediate actions against suspicious contacts
What: Report contacts or messages to WhatsApp and block a number.
Why it’s important Rapid blocking helps detect abuse more broadly by lowering the interaction surface with suspicious numbers. helpful for spotting attempts at social engineering that might result in WhatsApp hacking.
Setting instructions: Launch chat → Tap contact → Report/Block contact.
11) Backups: Protect and Encrypt (don't leave backups exposed)
What: Make sure backups are protected by a strong password or passphrase and encrypted.
Why it’s important Even without taking advantage of the active application, hackers can read previous messages if they manage to access your cloud backups. This is essential to guard against data theft brought on by WhatsApp hacking.
Setting instructions: Configuration → Chats → Chat backup → Activate end-to-end encrypted backup → Create a secure password.
12) App Permissions: Examine the Camera, Storage, Location, and Microphone
What: Verify which apps are authorized to use the microphone, camera, and storage.
Why it’s important Data exfiltration can be increased by combining a compromised WhatsApp with a malicious or compromised app that has access to the microphone and camera. Limit permissions to apps that are absolutely necessary.
Setting instructions: Phone Settings → Apps → WhatsApp → Permissions → Examine and remove any permissions that aren’t needed.
Permissions matrix with microphone/camera toggles and suggested safe settings is a visual suggestion.
13) Device Hardening & System Updates — The OS layer matters
What: Keep the OS patched; enable platform hardening features (e.g., iOS Lockdown Mode if applicable).
Why it matters: Many WhatsApp exploits chain into OS-level bugs. A patched OS closes escalation paths used in WhatsApp hacking.
How to set: Phone Settings → Software Update → Install latest updates.
FAQ (concise & focused)
Q 1.Will these settings prevent all WhatsApp hacking?
- No. They reduce risk and exposure. Combined with OS updates and vigilance they make hacking much harder.
Q 2.What should I monitor for in WhatsApp monitoring dashboards?
- Unknown linked devices, sudden data spikes, unusual outbound connections, and unexpected app crashes.
Q 3.If I see an unknown linked device, what next?
A . Revoke the session immediately (Settings → Linked devices → Log out) and change important passwords from a clean device. See /whatsapp-emergency-checklist.
Q 4.Do disappearing messages block spyware?
A .They limit retained data but don’t stop spyware already on a compromised device. Always combine with detection steps. See /check-whatsapp-spyware.
Q 5. One simple step to do right now?
A . Enable Two-Step Verification. See /whatsapp-two-step-setup.

